A cold wallet is usually a physical object: a cold card, joystick, or another device, that stores your private keys offline. The concept here is that if your private keys are kept offline, they cannot be hacked.
This is how cold wallets, especially cold hardware wallets, have an advantage of safety and security over hot wallets, also known as software wallets.
Hot wallets are always connected and store your private keys and seed phrases on their online platform, making them more susceptible to a cyber-attack.
But, as tech continues to evolve and the world of DeFi wallets expands, new vulnerabilities are always emerging even when we think our crypto is in a safe place.
So, this begs the question: can a cold wallet be hacked?
In this post, we will look into what is a cold wallet and how it functions and examine the potential threats that a cold wallet faces. We will explore real-world cases and share our secrets on how to store your crypto securely.
What Do We Mean By Cold Wallet?
The main idea behind any cold storage is to eliminate the threat of hackers getting to your private keys and stealing your crypto.

This is done by storing your private keys offline and ultimately not being connected to the internet to store your crypto, which in theory reduces the risk of cyber-attacks.
Types of Cold Wallets
Hardware Wallets
These are physical devices made for storing your crypto’s private keys. You only connect to the internet if and when you make a transaction. Popular hardware wallets include Material Bitcoin, Ledger, Tangem, and others.

➕Advantages
- High-security.
- Portability.
- Tangible object for keeping your crypto.
➖Disadvantages
- Costly (the initial upfront payment for the hardware device).
- Risk of physical damage or loss of object.
☝️We recommend using a separate wallet for storing your seed phrases, like Material DIY.
Paper Wallets
A paper wallet is a printed or written document that contains your private and public keys. This information is usually created by a software program.

➕Advantages
- Low cost.
- Offline security.
➖Disadvantages
- Fragile material.
- User error when printing (if printed on a public printer or exposed online when generating keys and QR Code).
Air-Gapped Computers
An air-gapped computer is a device that is never connected to the internet. It’s used to generate and store your private keys, make transactions, and sign them offline. These transactions are then transferred to an online connected device that sends it to the blockchain (usually with a USB or QR Code).
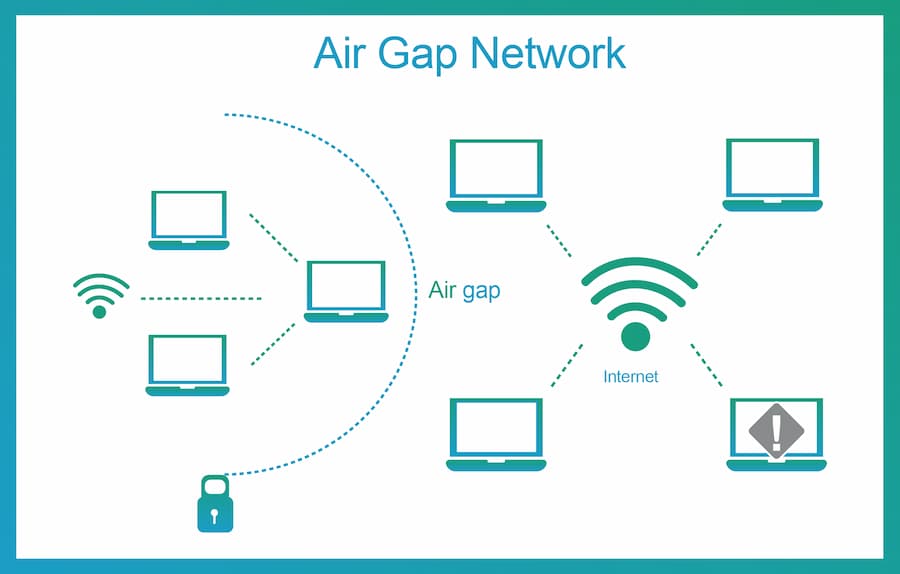
Image by rubrik
➕Advantages
- High Security
- Diveristy and versatility (can be used for storing private keys but also generating wallets and signing off on transactions).
➖Disadvantages
- Large and bulky machine.
- Complex setup for creating transactions, generating wallets, and maintaining air-gapped features from offline to online devices.
5 Potential Vulnerabilities of a Cold Wallet
While cold wallets are designed to provide the highest security measures for your crypto by keeping your private keys offline, they are not entirely free from vulnerabilities. Understanding these potential risks is crucial.
Let’s go over some cold wallet vulnerabilities and share some real-world examples so that you can learn from others’ mistakes.
- Physical Theft: This is probably the easiest way for a hacker get gain control of your private keys and crypto. If your cold wallet falls into the hands of a knowledgeable hacker, all they need to do is unlock your PIN and passcode.
🚨This is why seed phrase storage on a separate system is VITAL. If you lose your cold wallet or if it is physically stolen, you can recover your private keys and set them onto a new hardware wallet before the thief has a chance at it.
DO NOT EVER ENTER YOUR SEED PHRASE ONTO A DIGITAL DEVICE OF ANY KIND.
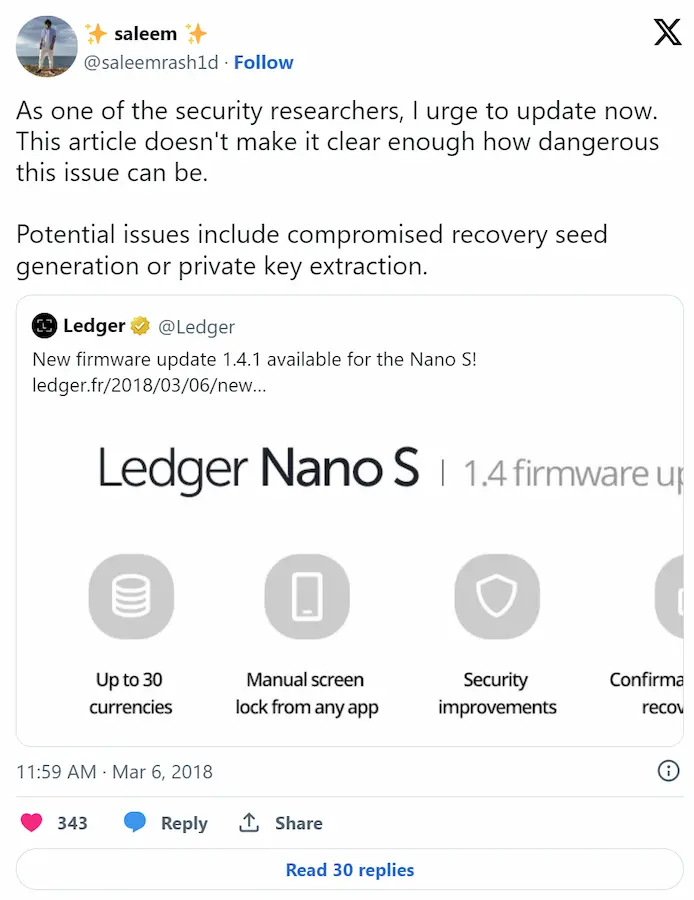
- Firmware Attacks: Hardware wallets that have software programs implemented into them can be vulnerable to firmware attacks if the attacker has physical access and can alter the device.
Probably the most famous firmware hacking is when a 15-year-old hacker named Saleem Rashid, unlocked a Ledger Nano S by uploading modified firmware onto the device that revealed the user’s private keys.
- Tampering in the Supply Chain: This happens during the production or the shipping process of the cold wallet before it reaches the customer.
Perhaps one of the “rarest” hacking vulnerabilities, it is still possible. Remember to always buy cold hardware wallets from authorized retailers and check that the package hasn’t been opened or tampered with.


In this example of tampering, the physical device had been modified in three ways to give access to the criminals: they disabled the protective mechanisms; replaced the random seed phrase with one of 20 pre-set phrases; and only used the first character of any additional password.
- Phishing Scams: hackers and scammers use pretenses like names, emails, websites, and phone calls, to trick you into revealing your private keys or seed phrases.
Unfortunately, this is probably the most common and easiest hacking trick in the book.
The responsibility is solely on you: the user, to be aware of fake accounts and personal in order not to give away your private info.
- Damage or Loss: Having your cold wallet damaged by simple wear and tear or elements, such as water or fire can be detrimental to its recovery. Lossing it all together without a proper recovery phase setup can lead to permanent loss of your funds.
Picking a strong hardware wallet that is water and fire-resistant is a good starting point for safeguarding your wallet. Keeping the physical device in a secret and safe location, like a security box at home is usually the best solution.
Simple Tips for Protecting Your Cold Wallet and Crypto
➡️ Use a reputable hardware wallet.
➡️ Always purchase hardware wallets from official and authorized retailers.
➡️ Verify the authenticity of the device upon receipt.
➡️ Enable PIN protection.
➡️ Set up a strong PIN.
➡️ Back up your recovery phrase, preferably on physical forms, like an engraved cold card.
➡️ Update firmware regularly.
➡️ Be cautious of phishing attempts.
➡️ Never share your private keys or recovery phrases with anyone.
Famous Hacks and How They Could Have Been Prevented
Over the years, there have been several high-profile hackings where cold wallets were compromised. Like the example we gave before with the Ledger Nona S and Saleem Rashid, many of these Bitcoin scams and frauds occur when there is a lack of user responsibility and device malfunction.
Here are some more real-world examples that will help give you further insight into hacking strategies and how you can learn from them.
The Kraken-Trezor Hack
Back in 2020, security researchers at Kraken intentionally found a vulnerability in a Trezor hardware wallet. They were able to extract the seed phrases on the device by using a voltage glitching technique. This type of hack involves manipulating the device’s power supply to cause errors that reveal your sensitive information.
A hacker would need to physically have your cold wallet to be able to use this method, but it highlights the importance of securing your physical device in a safe location.
You can watch how they did it here
Google App Store Vs. Hackers
In April of 2024, Google filed a lawsuit against a group of crypto scammers who have allegedly used phishing schemes to fraud over 100,000 people globally by uploading fake crypto exchange apps to the Google Play Store.
We know this example is not particularly linked to one certain cold wallet, but it goes to show that even trusted platforms can be vulnerable.
If your chosen hardware cold wallet relies on a downloaded app to make exchanges or trades, be certain that you are using the official app.
💪 Pro Tip: Using QR Codes that come with the physical device can ensure you are linking to the official app.
The Best Choice for Cold Storage
Unlike traditional hardware wallets, Material Wallets don’t have an electronic component nor do they require USB cables to connect to phones or computers to manage your BTC, ETHER, or USDT.
Instead, Material Wallets have a unique and highly secure solution to safeguarding your private keys and seed phrases by eliminating these sensitive attributes of some other cold wallets.
No Electronic Components
This means that Material Wallets are that much harder to hack since they can’t be susceptible to firmware attacks or have physical tampering. Unlike Trezor or other cold wallets, there are no wires or circuits to tamper with here.
No USB Connection Required
You never connect your cold wallet to your phone or a computer with any cable or USB joystick. Instead, if you want to manage your crypto, you scan a QR Code. This helps to reduce your private key visibility to online devices.
Top Security Combo
Using both the Material Cold Wallet with the Material seed phrare wallet is the ultimate in security. Both wallets are made of stainless steel, making them fire and water-resistant and able to withstand other physical damage.

Even if hackers get physical access to your Material Wallet, without the seed phrase recovery card, they won’t be able to access your private info.
FAQs
Are cold wallets really safe?
- Cold wallets are always going to be safer than hot wallets. Although, some cold wallets are considered safer than others.
Can a cold storage wallet break?
- Yes, if they are electronic devices, a hardware wallet can physically break. This is why using a cold card wallet and recovery phrase storage is the ideal choice for your crypto’s security.
What if my cold wallet is stolen?
- If your cold wallet is stolen, the thief would still need your PIN or recovery phrase to access your private keys. This again highlights the need for safe seed phrase storage.
Has a hardware wallet ever been hacked?
- There have been several instances where hardware wallets were compromised but, proper security measures will help to reduce these hacking attacks.
Your Takeaway on Cold Wallet Hackings
Can a cold wallet be hacked?
Yes.
But, staying up-to-date and informed on new hacking technologies, and scamming methods, in addition to using one of the best hardware wallets available with seed phrase storage will provide the best solution for keeping your crypto safe.








0 Comments