How to create a safe environment
Important: Before proceeding with this tutorial, make sure you have read and understood this Bitcoin and Cryptocurrency Security Best Practices Manual.
The advice provided on cryptocurrency and/or bitcoin trading is for informational and educational purposes only and does not constitute financial advice or investment recommendations. The cryptocurrency market, including bitcoin, is highly volatile and poses significant risks. Any investment decision or transaction made based on the provided information is the sole responsibility of the user. We strongly recommend conducting thorough research, consulting professional financial advisors, and considering your own financial situation and risk tolerance before engaging in any cryptocurrency and/or bitcoin-related activities. We are not responsible for any loss or damage resulting from the misuse of the provided information.
———————–
As you know, the most complicated part in the world of cryptocurrencies is to operate them safely in an environment where we do not run the risk that a virus or any type of malware that we have on the computer can give access to our funds to third parties.
That is why we are going to see some simple steps to have a very safe environment in our usual computer.
What is a secure environment?
A computer in a secure environment is:
– A computer disconnected from the Internet, bluetooth and any other kind of connection.
– With an operating system with minimal software installed and running in the background.
– Operating system with updated software.
What are we going to do?
The easiest way to achieve this is to use a Linux live USB and install the necessary software on the fly.
This will not affect our computer: it consists of obtaining a clean operating system very quickly, which we run from an external USB.
For this we will need a USB memory stick of a certain quality (with an advertising one there can be speed problems and crashes).
On that device we will install a version of the Linux operating system. We will boot the computer with the USB memory connected and, when booting, we will boot into a clean operating system, without the possibility of any virus from our computer affecting it or collecting information from what we do on it.
How are we going to do it?
Step 1: Once we have the USB memory we go to https://elementary.io/ and we download the system image file. We can contribute some money or give a custom price (which can be set to 0) and download elementary OS.
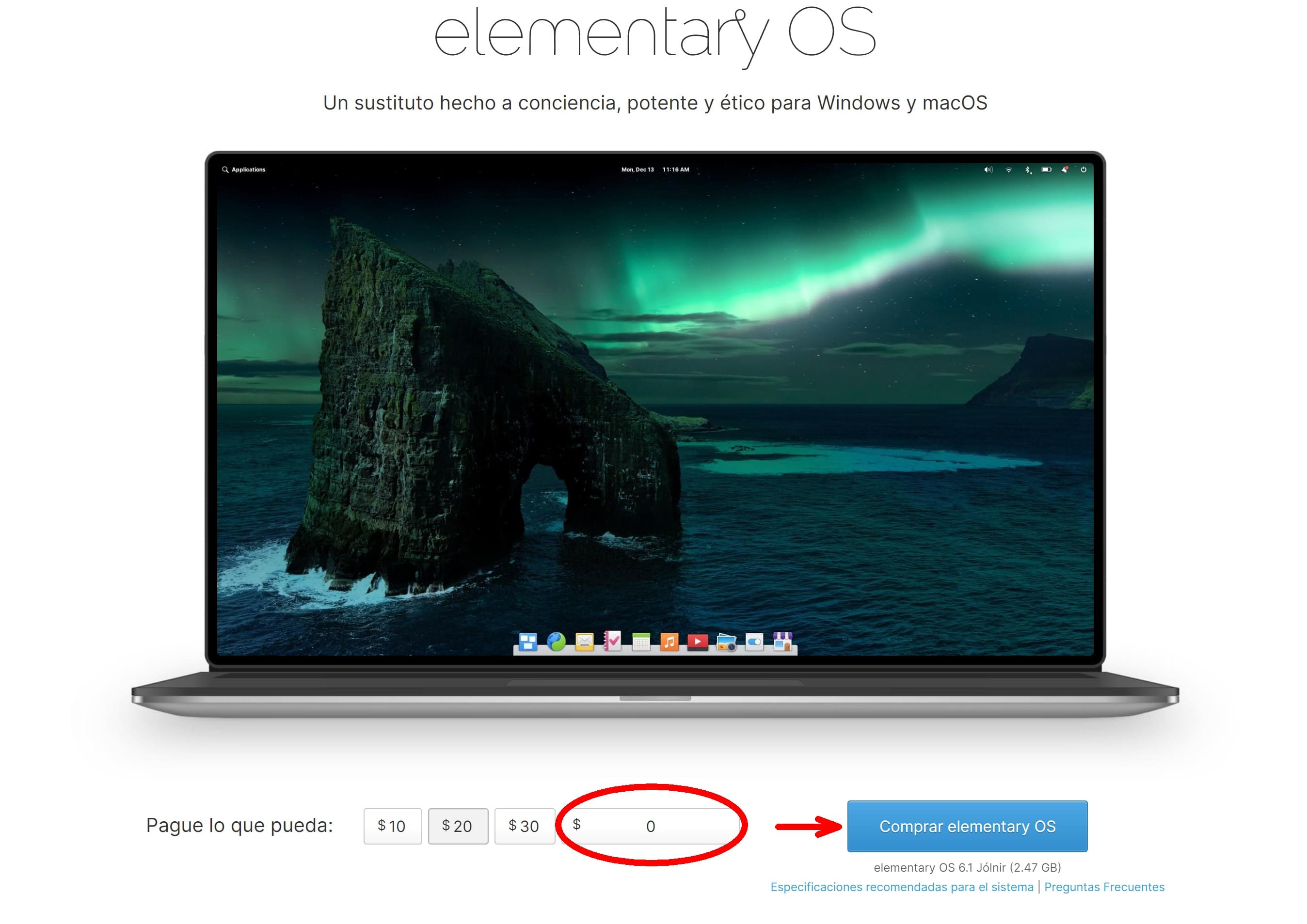
We are going to download the file into our computer, which we’ll use later to install the system into the USB Drive.
Step 2: Go to https://www.balena.io/etcher/ and download the appropriate program for your Operative System. This program will allow us to put Linux on the USB.
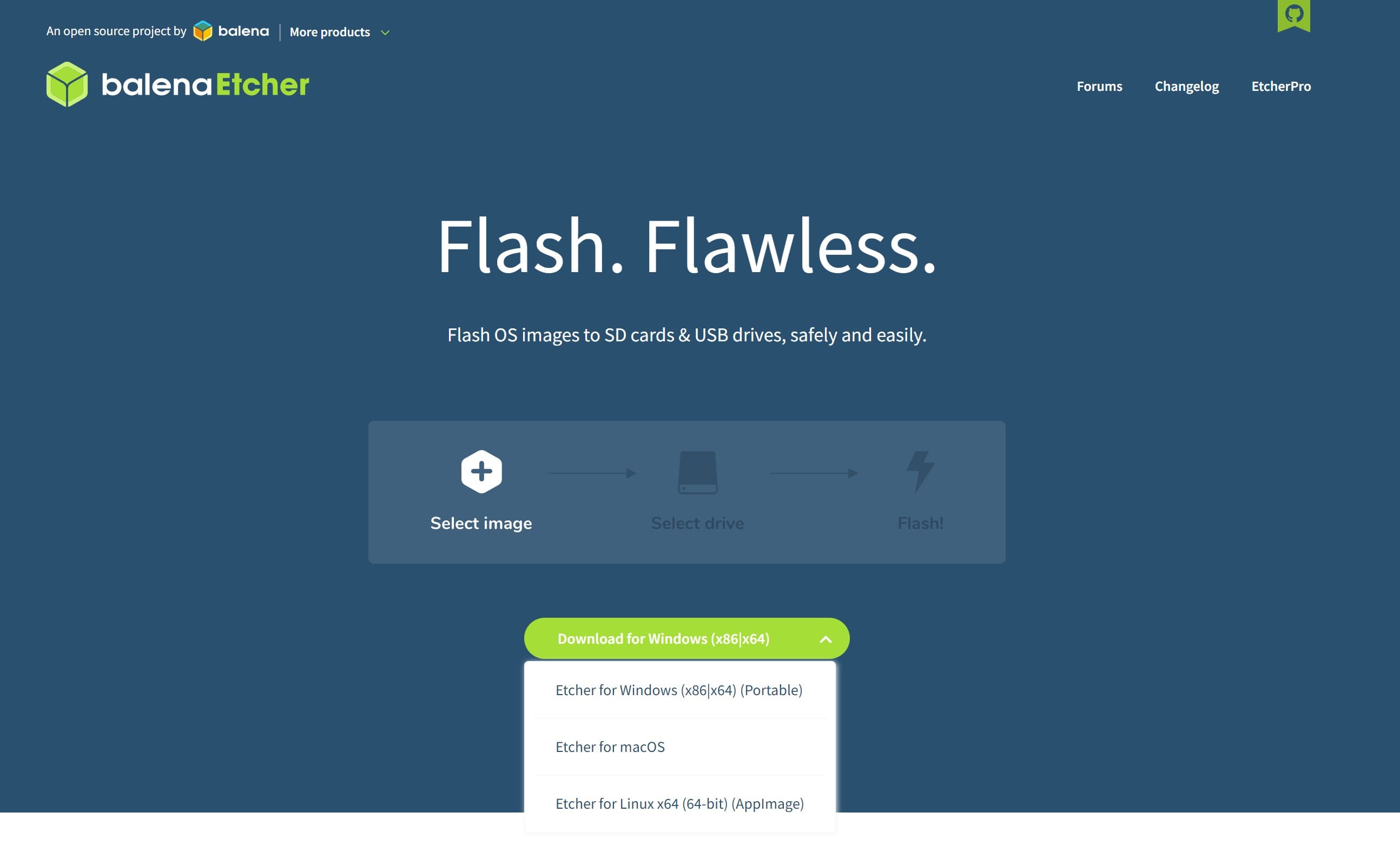
Step 3: We connect our pendrive to the USB port of the computer and run the balenaEtcher program we just downloaded.
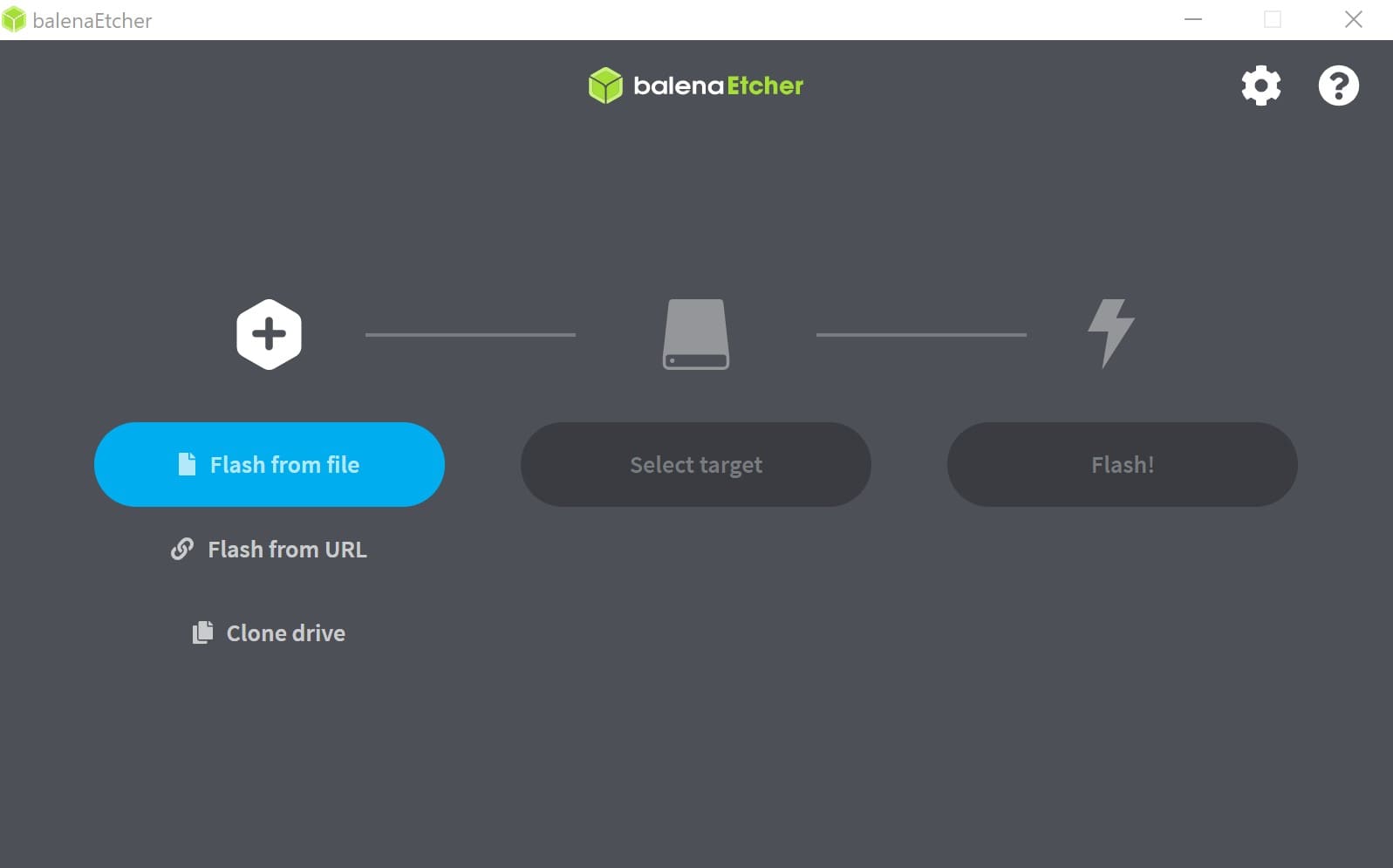
Step 4: We choose the Flash from file option and choose the file we have downloaded.
Then it asks us to choose the destination and we choose the directory of the pendrive and we execute. What it is going to do is to “put” the operating system in the USB pendrive.
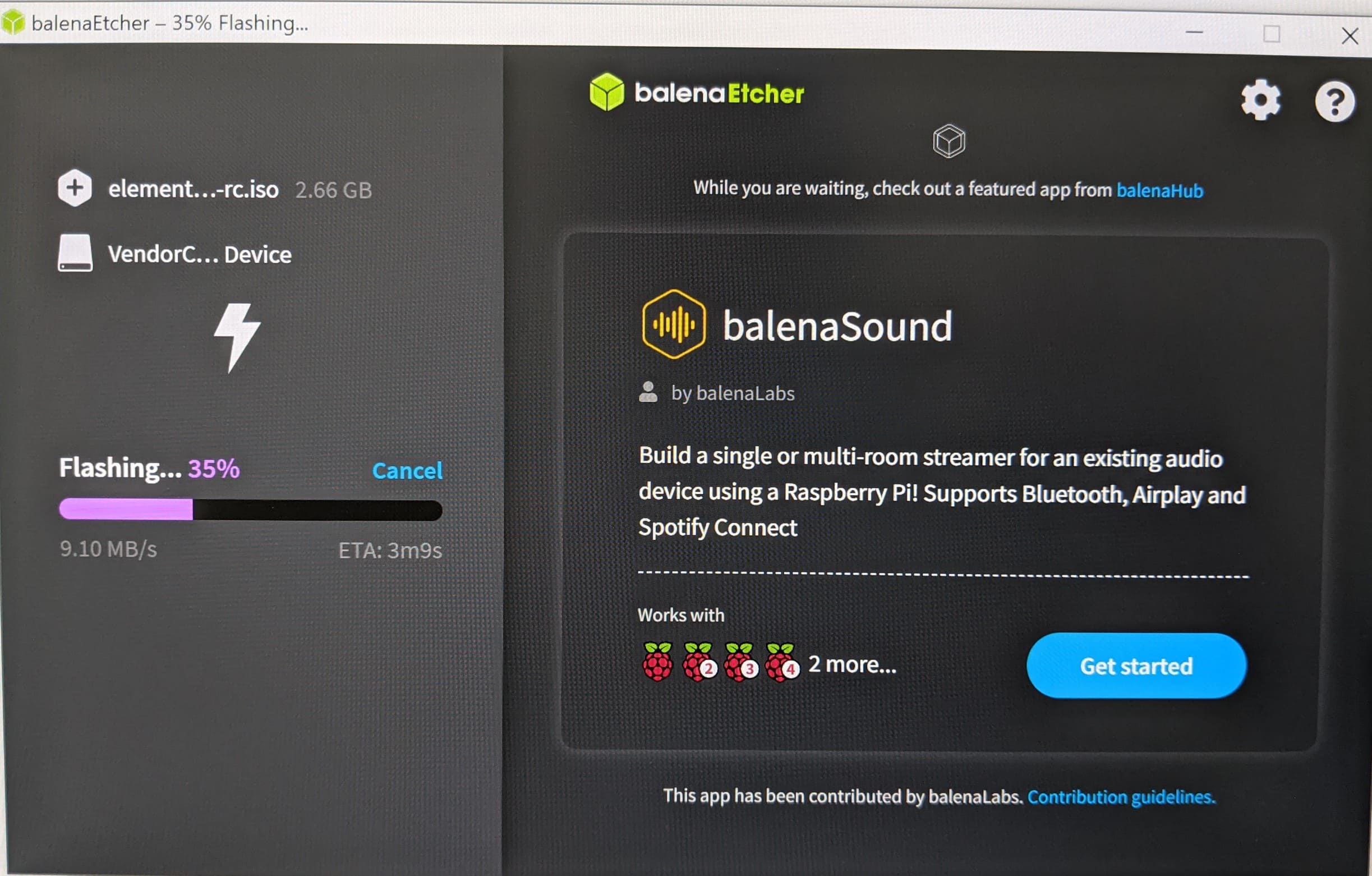
Step 5: Now we can turn off the computer. When we turn it on, we have to have the USB device connected and we will press F12 while the computer boots to open the Boot Menu(if your computer does not open this menu with F12 and boots normally, it may be another key such as F8, consult the characteristics of your computer’s manufacturer to know how to boot the operating system from the pendrive).
Step 6: It will ask us if we want to boot from USB.
We choose the option and when booting it will give us the option to install or try demo mode.
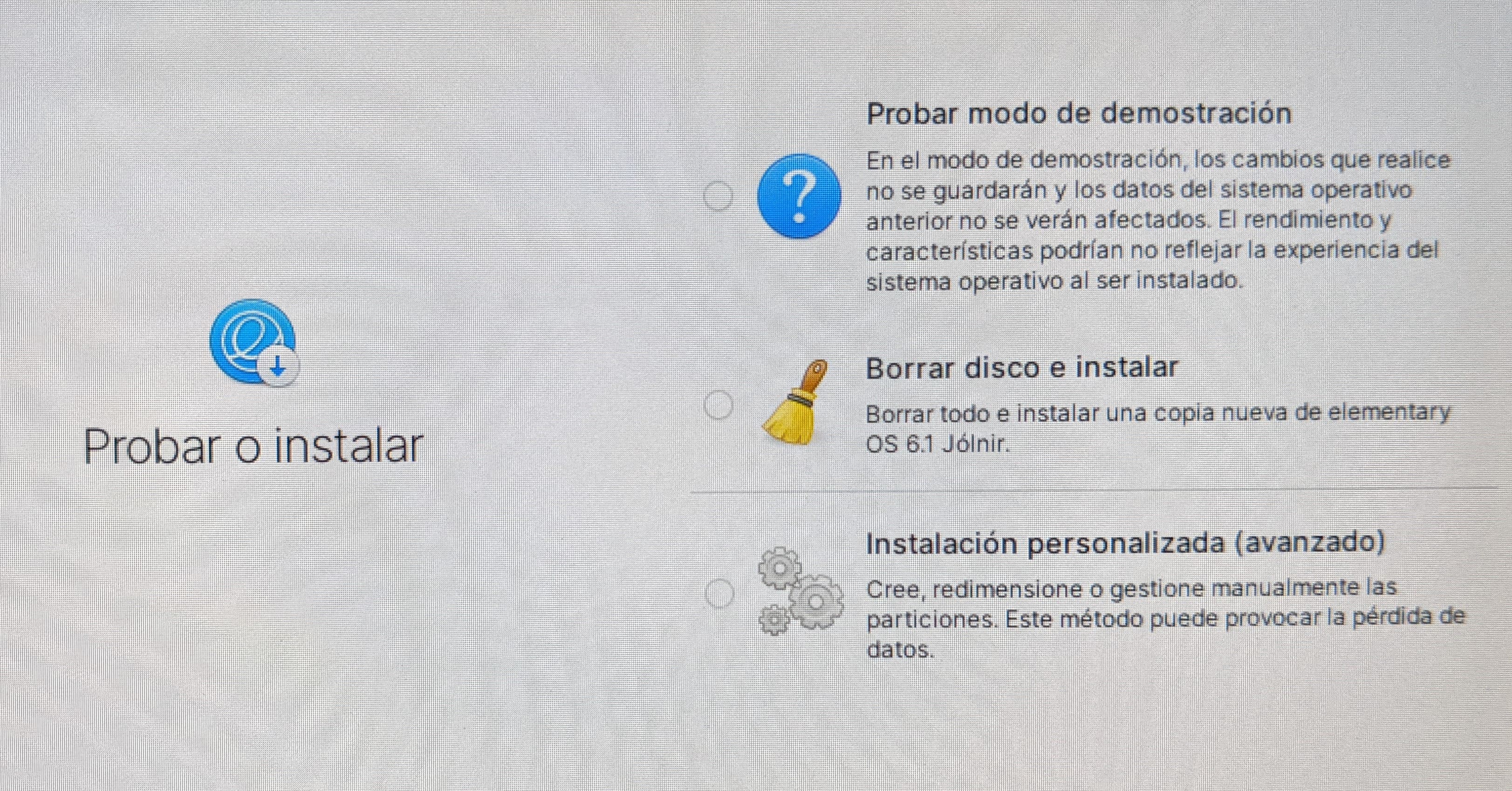
We choose the option to test in demo mode that Linux distribution from the USB, without installing it.
Last step: Once started, we connect to the internet and we can download the Brave browser, the Metamask wallet or Electrum.
Once we have everything installed, we disconnect the internet, remove the cameras that can “snoop” on what we are doing and generate our passwords as we explained in the tutorial on how to generate your wallet.
Everything can be done safely and, when we turn off the computer, the USB with Linux will not remember anything and will be as good as new.
Need help? Leave us your question
To receive immediate help from our community at any time, please join our Telegram group.




